Deploy reverse proxy
version: '3'
services:
app:
image: 'jc21/nginx-proxy-manager:latest'
restart: unless-stopped
ports:
- '81:81'
- '80:80'
- '443:443'
volumes:
- data:/data
- letsencrypt:/etc/letsencrypt
networks:
proxy:
ipv6_address: 2a01:4f8:c013:ae57:0001::3
volumes:
data:
letsencrypt:
networks:
proxy:
external: true
docker-compose up -d
Access NGINX proxy manager on: http://a01.labs.innog.net:81 and login with username admin@example.com and password changeme
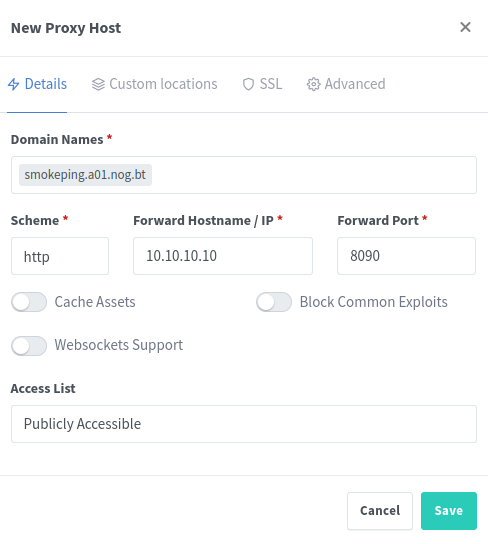
- Click on hosts
- Select proxy hosts
- Add proxy host
- Add uptime.a01.labs.innog.net in the domain names
- In the Forward Hostname / IP put 10.10.10.10 and in forward port put 8090
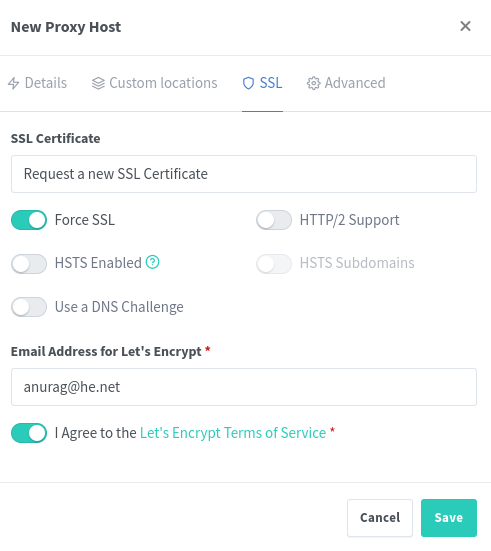
- Click on SSL tab and select request new SSL certificate
- Check “force SSL” and agree to the Letsencrypt terms
- Click save and wait for reverse proxy vhost to be deployed with a TLS certificate
Once done, ensure that you are able to access your app on https://uptime.a01.labs.innog.net
Reverse proxy NGINX proxy manager behind itself. Use 10.10.10.10 port 81 and proxy the hostname npm.a01.labs.innog.net
Ensure that port 81 is bind only on loopback IP i.e 10.10.10.10 for NGINX Proxy manager and port 3001 is only bind to 10.10.10.10
Updated config for ports will look as:
NGINX Proxy Manager
ports:
- '10.10.10.10:81:81'
- '80:80'
- '443:443'
Uptime Kuma
ports:
- '10.10.10.10:3001:3001'
- '80:80'
- '443:443'
This will ensure NGIX proxy manager admin or uptime kuma is not available over any direct access anymore.